Ping Trace
Project Title: Ping Trace
Technology Used: Python, Raw Sockets, ICMP, Network Programming
Overview
Ping Trace builds upon a raw socket ICMP ping implementation to offer traceroute functionality. The project sends ICMP echo requests with incrementing TTL values to track the network path from the source to a destination. Intermediate routers respond with ICMP Time Exceeded messages, while the final destination replies with an ICMP Echo Reply. The tool validates responses and aggregates key statistics, including round-trip times and packet loss.
Features
- Utilizes raw socket programming in Python to construct and send ICMP packets.
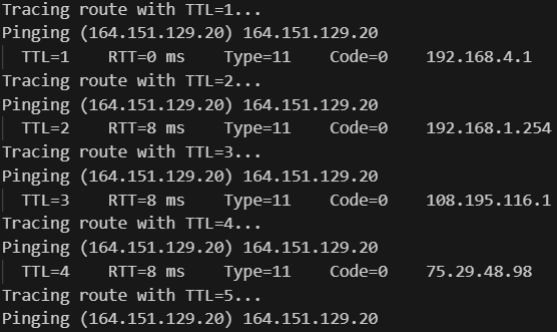
- Implements traceroute functionality by incrementing TTL values to discover intermediate hops.
- Processes multiple ICMP response types: Time Exceeded (type 11) for intermediate routers and Echo Reply (type 0) for the destination.
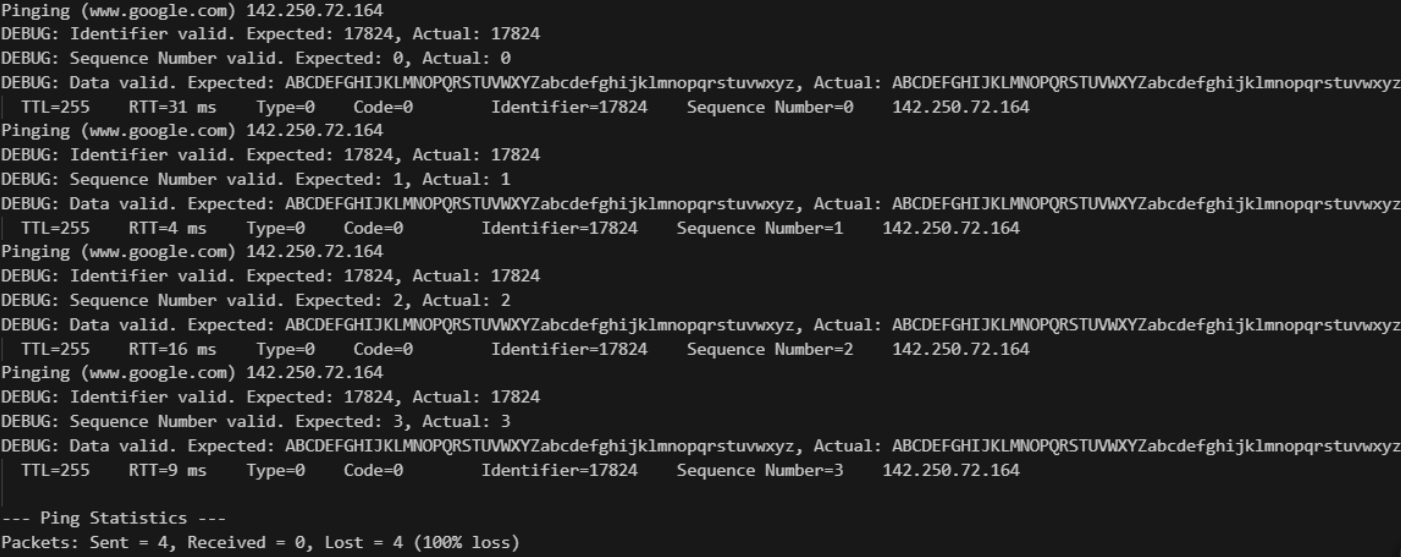
- Validates responses by comparing packet identifiers, sequence numbers, and embedded data.
- Calculates individual round-trip times and aggregates statistics such as minimum, maximum, and average RTT, along with packet loss rate.
- Handles error responses, including Destination Unreachable (ICMP type 3), for robust performance.
Code Overview
The project is organized around the IcmpHelperLibrary class, which encapsulates
both
ping and traceroute functionalities. Nested classes manage the creation, sending, and validation
of ICMP packets. Core operations include checksum calculation, raw byte data manipulation, and
network response handling. This structure demonstrates an effective application of low-level
network
programming in Python.
Screenshots
Below are sample outputs from Ping Trace:
Interested in More?
Source Code: Ping Trace